LucidShell - A memory-safe Rust-based Windows security shell for white-hat use
⚓ Rust 📅 2025-11-05 👤 surdeus 👁️ 25I’m excited to share a new open-source project: LucidShell (GitHub: LucidShell) - A high-performance, memory-safe, sandboxed security shell built entirely in Rust for Windows.
LucidShell is aimed at authorized penetration testing, digital forensics, auditing and red-team operations where legal compliance and evidence handling matter. (Yes: white-hat only.) You’ll find features such as:
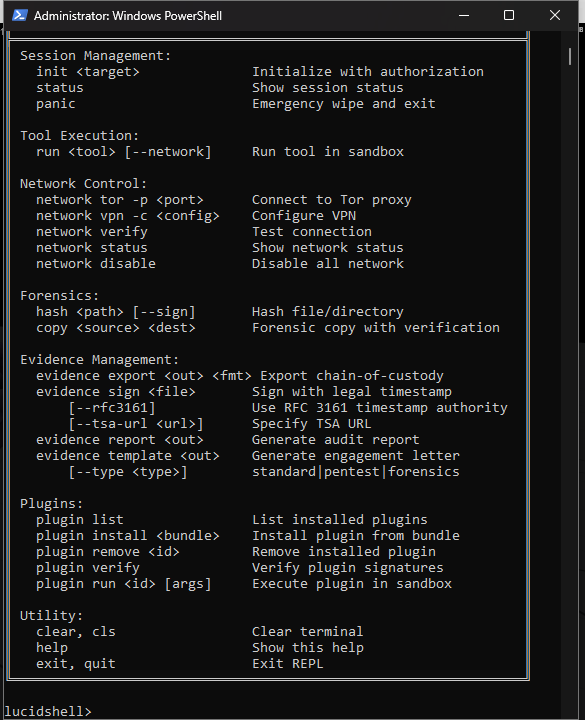
- Session management (
init,status,panic,repl, etc) - Tool execution with sandbox profiles (minimal/standard/elevated)
- Network controls (Tor, VPN support)
- Forensics operations (mount, hash, copy with integrity checking)
- Evidence management (export, sign, report with chain-of-custody)
- Plugin system (install/verify/run plugins in sandbox)
Note: Some advanced sandboxing and container encryption features are still work in progress.
By writing this entirely in Rust, my goals are:
- Memory safety: avoid classic C++ bugs in security tooling
- Performance: low overhead for real-world engagements
- Modern ecosystem: leverage Rust’s tooling, crates, cross-platform potential (though currently Windows only)
- Easier maintenance: safer code base and fewer vulnerabilities
Use cases
- Red-team or penetration testing engagements
- Digital forensics with audit trail & legal defensibility
- Security auditing in Windows environments
- Incident response where evidence chain matters
Current status & roadmap
- Version: v0.1.5 released (Windows only).
- Sandbox isolation: job objects work, but full filesystem/registry restrictions are still a TODO.
- Container encryption: existence verification works, decryption logic still forthcoming.
- Plugin execution: install/verify works; full sandboxing of plugin APIs is pending.
Full details in the README.
Why I’m posting here
I’d love feedback from the Rust community. Roast me!;
- Does the architecture feel idiomatic Rust?
- Any crates or patterns you’d recommend?
- Would you consider using this tool in your workflow, or contributing?
- Ideas for making it more “Rust-y”, more secure, more community-friendly?
License: GPL-3.0
Feel free to open issues, pull requests, or start discussions. I’m happy to collaborate!
Thanks for your time, and I hope you find it interesting!
1 post - 1 participant
🏷️ Rust_feed